Ensuring the security of your software development projects requires more than just using the right tools. It means a comprehensive approach covering everything from coding practices to infrastructure security to proactive testing and monitoring. This blog will walk you through an extensive checklist to keep your applications safe.
We’ll explore several core areas, including Secure Coding Practices, Authentication and Authorization, Data Protection, Security Testing, Infrastructure Security, Incident Response and Monitoring, Training, and Continuous Improvement.
Summary
- Secure Coding Practices: Learn the importance of code reviews, input validation, and managing dependencies to prevent vulnerabilities.
- Authentication and Authorization: Discover robust session management, role-based access, and multi-factor authentication techniques.
- Data Protection: Understand data encryption, retention policies, and access control to safeguard sensitive information.
- Security Testing: Explore methods like SAST, DAST, and penetration testing to identify and fix security flaws.
- Infrastructure Security: Implement strategies for network segmentation, firewall configuration, and endpoint security.
- Incident Response and Monitoring: Develop effective monitoring, logging, and incident response plans to handle security breaches.
- Training and Continuous Improvement: Engage in regular security training and establish feedback loops to maintain high-security standards.
TLDR – Download the Checklist
Does this blog seem too long? No worries – Download our app security checklist.
Secure Coding Practices
To kick things off, let’s talk about how you can start thinking about security while the code is being written. Developers, this one’s for you!
Code Reviews
Having a senior-level developer review your code on every check-in is a must. Having a second pair of eyes helps you catch any security flaws early on and ensures you follow best practices. Automated tools might miss some of these issues, so a good old-fashioned human review can go a long way in identifying potential vulnerabilities.
Input Validation
Ensuring the security of your applications means meticulously validating all user inputs. This validation means checking the length, format, and type of data entered before it is processed or stored in your database. Such validation is essential for preventing common security threats like SQL injection and cross-site scripting (XSS).
Scrub and transform data as part of your input validation process. This step means sanitizing the data to remove or encode harmful elements that bad actors could use in injection attacks. Whenever possible, utilize the scrubbing and transformation functionalities provided by your Object-Relational Mapping (ORM) tool. These built-in tools can handle data safely, reducing the risk of SQL injections by properly escaping parameters.
Moreover, implementing systems to monitor incoming requests can significantly enhance your security posture. For example, using a Web Application Firewall (WAF) like AWS’s WAF can help detect and block malicious traffic and attacks before they reach your application. By combining rigorous input validation, data transformation, and active monitoring, you can create a robust defense against many common vulnerabilities that threaten web applications.
Dependency Management
It’s essential to keep all your software dependencies up to date. That means you should update your NuGet and NPM packages regularly to avoid issues with older versions. Keeping up-to-date will help you stay secure and prevent any vulnerabilities that might be present in outdated libraries.
Managing Secrets
Protect sensitive data, such as passwords and API keys. Encrypt these secrets always and avoid storing them directly in your source code. Only give access to such confidential information to individuals who require it for their role.
Furthermore, you must ensure you don’t reuse secrets between different environments, including development, testing, staging, and production. Each environment should have its unique set of secrets to minimize risks. Sharing secrets between environments, particularly between development and production, can lead to significant security vulnerabilities.
Development environments are generally more vulnerable to attacks, and if they’re compromised using the same secrets as production, it can lead to unauthorized access to critical systems. By maintaining separate secrets for each environment, you can reduce the possibility of a single breach compromising multiple areas of your infrastructure.
Authentication and Authorization
Securing an application requires effective authentication and authorization practices. These should involve robust session management, strict access controls, strong authentication measures, and multi-factor authentication. Together, these strategies form a comprehensive approach to protecting sensitive data from unauthorized access.
Session Management
Robust security measures are crucial for effectively managing user sessions. To ensure user cookie security, encrypt cookies and restrict access to HTTPS connections only. Moreover, implementing automatic logout mechanisms after a period of inactivity is a practical way to prevent unauthorized access to user accounts.
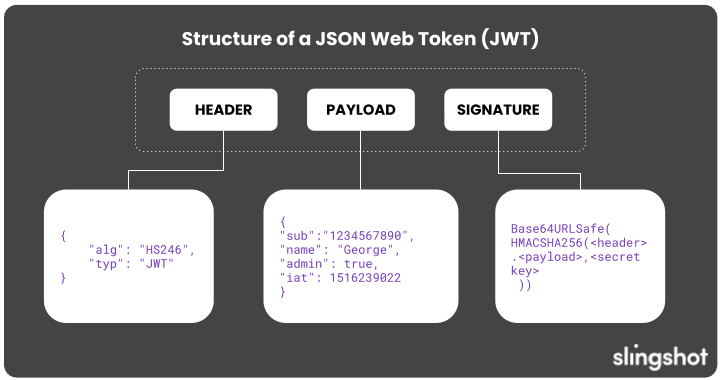
The specific implementation of these measures can vary based on the technology stack used. For example, using JSON Web Tokens (JWT) with token checksum validation provides a robust way of handling session security and user authentication. Nevertheless, it’s essential to note that not all applications will utilize JWTs. Therefore, it’s crucial to tailor your session management strategy to align with your particular architecture and security requirements, ensuring that all precautions are practical and aligned with industry best practices.
Role-Based Security
Access controls are a fundamental security aspect, ensuring users access only the resources necessary for their roles. This concept, known as the principle of least privilege, restricts user permissions to the bare minimum required to perform their jobs effectively, thus minimizing the risk of accidental or malicious data breaches.
However, access controls should be robust at the application level and consistently enforced at the backend. An often-overlooked vulnerability occurs when front-end applications are secured, but the APIs they interact with remain unprotected. This discrepancy can lead to unauthorized data access through the backend, even if the front-end systems appear secure.
Backend systems require authentication and authorization mechanisms to secure APIs. You can utilize API keys, JWTs, and OAuth tokens for authentication. Role-based access Control (RBAC) policies limit user access based on their roles. Audit trails maintain data access logs for security monitoring and deterrents against unauthorized access.
Increase Entropy
Increasing entropy through solid and complex passwords is crucial for safeguarding your systems from unauthorized access and potential hacking attempts. This principle primarily applies to user account security, where enforcing strict password policies is essential to protect sensitive data.
To ensure that all passwords meet the highest security standards, you’ll want to implement policies that require passwords to be at least 12 characters long, including a mix of uppercase and lowercase letters, numbers, and special characters to enhance their complexity. Additionally, policies should prevent using commonly used or easily guessed passwords, such as “password123” or “123456”. Encouraging or requiring users to change their passwords regularly can also help.
Still, frequent intervals that lead users to choose weaker passwords or repeat patterns are essential. Implementing these password policies through technical controls within the authentication system ensures that users can only set passwords that comply with these guidelines. Using password managers can also help users generate and store complex passwords, reducing the likelihood of reuse across different sites and systems, thus enhancing the overall security posture of your applications and infrastructure.
Authentication
Requiring Multi-factor Authentication, or MFA, to make your software more secure is a good idea. This way, even if someone gets hold of login details, they won’t be able to access the software without the additional information. Also, use Google, Apple, or Facebook login instead of custom authentication when possible. These third-party logins will typically have extensive security mechanisms in place.
Account Change Notifications
It’s crucial to implement notifications for any changes made to user accounts. Users should receive immediate email alerts if any modifications occur, ensuring they are aware of unauthorized changes and can react swiftly to secure their accounts.
Login Notifications for New Devices
Receiving login notifications for new device accesses is crucial for maintaining online security. Whenever someone logs into their account from a new device, they should be alerted so they can confirm the activity or address any potential security breaches promptly. This simple step adds an extra layer of security by informing users of unfamiliar logins and allowing them to take necessary actions immediately.
Data Protection
Protecting data is a pivotal aspect of maintaining trust and ensuring integrity. You’ll significantly enhance your cybersecurity defenses by implementing effective data protection measures within your software systems. This action ensures that sensitive information remains secure and that you maintain user trust.
Data Encryption
Ensuring the security of your sensitive data involves implementing robust encryption strategies, both when the data is at rest and during its transmission.
Encryption at Rest refers to encrypting data stored on physical or virtual storage. Robust encryption protocols such as AES (Advanced Encryption Standard) with a 256-bit key ensure that data remains secure, even if the storage medium is compromised. This level of encryption is crucial for databases, file servers, and any backups containing sensitive or personally identifiable information. Disk and database encryption can significantly reduce the risk of data breaches by making the data inaccessible without the correct decryption keys.
Encryption in Transit means protecting data as it travels across networks to safeguard it from interception or tampering. Protocols such as TLS (Transport Layer Security) for web applications, IPSec (Internet Protocol Security) for network communications, and SSH (Secure Shell) for remote administration ensure that data is encrypted effectively during its transit. Additionally, ensuring that all data transfers employ secure methods and require authentication and integrity checks helps maintain confidentiality and trustworthiness of the data in transit.
Data Retention
Effective data retention policies are crucial for minimizing risk and ensuring compliance with regulatory requirements. These policies dictate how long you should retain data, aiming to balance between keeping it as long as necessary without holding onto it for too long. Managing data retention involves assessing the types of data you collect and identifying the legal, operational, and business requirements for retaining each category. This assessment helps define clear rules for how long your team should store different data types.
Ensure that your data retention policies comply with all applicable laws and regulations, such as understanding industry-specific rules that may dictate minimum or maximum retention periods for specific data types, such as financial records or personal health information. Limiting the duration that you keep data reduces the window of opportunity for unauthorized access and data breaches. Implement automated processes to delete data that has reached the end of its retention period. Automation ensures data deletion adheres to the established policies and is performed consistently without manual intervention.
Data retention policies should not be static. Regular reviews are necessary to adapt to changing legal requirements, business needs, and technological advancements. These double-checks ensure that the policies remain relevant and effective in managing risks associated with data storage. By setting and enforcing appropriate data retention rules, you not only comply with legal obligations but also enhance the security and efficiency of your data management practices, ensuring that you’re protecting sensitive information throughout its lifecycle.
Data Access
Restricting database access is crucial for maintaining security and operational efficiency in software development projects. Implementing role-based access controls (RBAC) is essential for effectively managing who can view or modify sensitive information. This approach ensures that access is granted based on the user’s role within the organization, allowing only those who need it for their job functions to access sensitive data.
For secure database access, using accounts with minimal necessary permissions is essential. Avoid using high-privilege accounts like ‘SA’ (System Administrator) for application connections; instead, create specific roles with only the permissions required to perform their functions. Continuous monitoring of database access is vital.
Utilize AWS CloudWatch to monitor access logs by configuring your database to output logs to CloudWatch. This tool allows you to set up alerts for specific events, such as root user connections or developer logins at unusual times, helping detect unusual access patterns or unauthorized attempts that could indicate a breach. For more advanced alerting capabilities, you can integrate tools like DataDog or customize Grafana to parse logs and extract detailed information, such as IP addresses.
Setting up real-time alerts for suspicious activities enhances your ability to respond swiftly and effectively to potential security incidents. Tools like IBM Guardium can monitor databases and generate alerts for unauthorized access attempts or anomalous activities, significantly strengthening your database security and ensuring data integrity. This proactive approach is crucial in maintaining the security of your software development projects and safeguarding sensitive data from potential threats.
Backups
It’s crucial to take the necessary measures to keep your data safe and maintain its integrity and accessibility. One effective way to do this is by making sure your backups are encrypted and resistant to unauthorized access. To ensure maximum security, you’ll want to keep the keys that unlock your encrypted backups offline and stored in a secure location. Doing so lets you rest assured that your valuable data is safe and always available when needed.
Security Testing
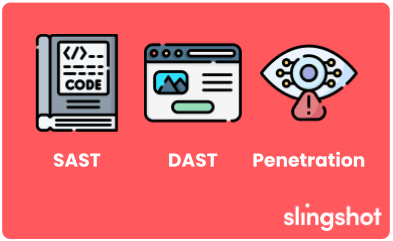
Ensuring the security of your applications is paramount, and employing a robust testing strategy is vital. Static Application Security Testing (SAST) examines the source code before execution to identify potential flaws, while Dynamic Application Security Testing (DAST) assesses the application during runtime to detect exploitable vulnerabilities. Additionally, penetration testing offers a comprehensive approach by simulating cyber attacks to identify security weaknesses.
Integrating these methods—SAST, DAST, and penetration testing—into your security regimen will provide a well-rounded defense against cyber threats and ensure your applications are secure and resilient.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) tools are essential for identifying potential security vulnerabilities directly within the source code without the need to execute the code. These tools analyze your codebase for patterns that may indicate security issues, such as improper input validation, insecure handling of data, or other common vulnerabilities that attackers could exploit.
To integrate security seamlessly into the development process, conducting SAST during every code check-in is advisable. You can automate this routine within your development environment to ensure that vulnerabilities are detected and addressed promptly, ideally before merging the code into your main branch. Examples of practical SAST tools include SonarQube, which offers comprehensive code quality and security scans, and Checkmarx, known for its ability to handle large codebases and provide detailed vulnerability assessments. Another popular choice is Veracode, which offers static and dynamic analysis capabilities, making it a versatile option for organizations looking to bolster their application security.
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) tools are crucial for scanning your application for vulnerabilities while running, simulating an attacker’s perspective. DAST tools interact with an application from the outside, examining the app as it runs to identify security flaws without needing access to the underlying source code. This method is particularly effective in detecting issues like SQL injection, cross-site scripting (XSS), unprotected APIs, and other vulnerabilities that bad actors could exploit once the application is operational.
With each new release, you should utilize DAST tools to ensure your app’s comprehensive safety. This continuous security testing helps catch any new vulnerabilities that could have arisen during development. Popular DAST tools include OWASP ZAP (Zed Attack Proxy), open-source and widely used for its extensive testing capabilities, and commercial solutions like Acunetix and Burp Suite, which offer more automated features and advanced user interfaces.
Penetration Testing
Penetration testing should ideally be conducted at least once annually, if not quarterly, by an independent third party to identify security vulnerabilities and evaluate the effectiveness of existing security measures. Companies like Kobalt specialize in these services, employing skilled, ethical hackers who simulate realistic attack scenarios to uncover potential weaknesses in your security defenses.
This approach is not just a routine test; it involves professionals using various tools and techniques to attempt to breach your systems as a malicious hacker would, focusing on exploiting any vulnerabilities, including those listed in the OWASP top 10. By engaging third-party experts to perform these tests, organizations can gain an objective assessment of their security posture, allowing them to address vulnerabilities in a controlled environment. This proactive strategy enhances security and ensures readiness for new threats and technological changes.
Infrastructure Security
Securing your software’s critical infrastructure is essential. Effective strategies include implementing network segmentation, configuring firewalls based on the principle of least privilege, installing intrusion detection systems, and ensuring that all software and operating systems are consistently updated. These measures help prevent malicious attacks and unauthorized access, safeguarding your infrastructure from potential threats.
Network Security
Enhancing network security by segmenting your network into distinct zones and deploying strategically configured firewalls can significantly strengthen the protection of sensitive systems. Network segmentation involves dividing the network into separate segments based on function or security level, isolating systems from each other, and minimizing potential breaches’ impact. Each segment can have tailored security policies, ensuring access is strictly controlled and limited to necessary communication.
It’s crucial to configure firewalls to enforce these segmentations effectively. You should set up firewalls that only allow the essential traffic required for each network segment’s operations. This security measure means implementing strict rules that govern data flow between segments and blocking unauthorized attempts to access sensitive areas of the network. These measures help manage traffic more efficiently and significantly reduce the risk of unauthorized access, keeping your critical data and systems secure from potential threats.
Endpoint Security
Endpoint security is critical for protecting software on devices from cybersecurity threats. This step involves deploying advanced endpoint protection solutions that can detect, analyze, and respond to security incidents on the device level. These solutions should include features like real-time threat detection, antivirus and anti-malware scanning, and behavioral monitoring of applications to prevent unauthorized access and activities.
Intrusion Detection Systems (IDS) are critical in identifying potential threats by monitoring network traffic and system activities for suspicious behavior. In the AWS environment, basic IDS functionality is provided within the Web Application Firewall (WAF) for web applications. However, third-party solutions might be necessary for more advanced IDS capabilities or coverage beyond web apps. It’s essential to configure IDS solutions to effectively recognize signs of security breaches, such as unusual access patterns or modifications to critical system files, and to alert security personnel to these activities. AWS offers DDoS protection through AWS Shield, which focuses on attack vector prevention rather than detection.
Regular updates to software and operating systems are essential to maintaining security. These updates often include patches for vulnerabilities that attackers could exploit. Ensuring that all endpoints are consistently updated minimizes the risk of security breaches that exploit outdated software components.
Assigning specific monitoring responsibilities to skilled personnel is vital for an effective security strategy. This dedicated team should have the tools to track security alerts and respond promptly. A systematic approach to monitoring ensures that you’re reviewing all alerts thoroughly, enabling quick action to mitigate potential threats and maintain the system’s integrity.
Incident Response and Monitoring
Monitoring activity and keeping detailed logs are crucial for good security. Having a solid response plan and regularly practicing it ensures you’re prepared to take action. These measures minimize the impact of incidents and improve your overall security.
Monitoring and Logging
Effective monitoring and logging are critical for promptly identifying and responding to security issues in your software development projects. Implementing comprehensive monitoring tools allows you to observe system operations and detect unusual or suspicious activities continuously.
Widely used tools include AWS CloudWatch, Grafana, Splunk, Datadog, and the ELK Stack (Elasticsearch, Logstash, Kibana). These tools are popular for their robust logging capabilities and real-time monitoring features. CloudWatch can aggregate logs from various AWS sources and provide monitoring and alerting. These tools can aggregate logs from various sources, providing a centralized platform for analysis and enhancing your ability to maintain secure and efficient software development environments.
In addition to monitoring, setting up proactive alerting mechanisms is crucial. You should configure systems to automatically notify your security team of potential threats as they are detected. Alerting ensures that any anomalies are not just logged but acted upon swiftly. This proactive approach minimizes the response time to potential security breaches, enhancing your organization’s overall security posture.
Incident Response Plan
Having a well-developed incident response plan is essential for effectively managing security breaches. This plan should outline specific procedures for detecting, reporting, and responding to security incidents to minimize damage and recover from attacks. Critical components of an incident response plan typically include identifying roles and responsibilities, communication protocols, steps for containment and eradication of threats, and strategies for recovery and post-incident analysis.

Your IRP will only be effective if you regularly test it. Tabletop disaster recovery exercises are one effective method for testing an incident response plan. These exercises require significant personnel to discuss simulated security scenarios in a structured environment and walk through the theoretical response step-by-step. The objective is to identify gaps or weaknesses in the plan and provide a practical, low-risk method to train staff on their roles during an incident.
Training and Continuous Improvement
Continuous education and improvement are vital in cybersecurity, especially for developers and tech staff. Regular training and feedback cycles ensure every team member understands the latest security practices and technologies.
By emphasizing the importance of security in the development teams’ daily work, this approach helps cultivate a proactive security culture within the organization, laying the groundwork for robust defense mechanisms and enhanced software security over time.
Security Training
Developers must be well-informed about the latest security threats and prevention techniques to keep their systems secure. Regular training sessions should cover topics such as secure coding practices, the latest cyber threats, and how to implement adequate security measures. Tools like Codecademy or Pluralsight offer comprehensive courses on cybersecurity that you can integrate into development training programs. Additionally, participating in security workshops and webinars provided by experts in the field, such as those offered through SANS or CompTIA, can provide valuable real-world insights and practical skills.
Feedback Loop
Continuously improving security practices is essential and requires a structured feedback loop. After any security incident or testing phase, gather insights and lessons learned to refine your security strategies. You can use tools like Jira or Trello to track feedback and suggestions for improvement effectively.
You should also have regular retrospective meetings to discuss what was effective, what wasn’t, and how you can improve your security processes. This feedback loop helps fine-tune security measures and promotes a culture of improvement and accountability within your team.
Security Champions
It’s a good idea to designate security champions within your development teams. These champions can be responsible for promoting and ensuring that everyone on the team follows the best security practices. By having security champions, you can improve your organization’s overall security posture and ensure that your team includes security in every stage of the development process rather than being an afterthought. These champions can also help to identify potential security vulnerabilities and work with the development team to address them before they become a problem.
Conclusion
In conclusion, the Essential Security Checklist for Software Development provides a robust framework for comprehensively securing your applications. Adhering to best practices such as secure coding, authentication, data protection, security testing, infrastructure security, incident response, and continuous improvement can help you safeguard your projects from potential threats and minimize risks.
Implementing this checklist is not a one-time task but a continuous commitment to maintaining high-security standards and adapting to evolving threats. By staying vigilant and proactive, developers and IT managers can ensure their applications remain resilient against vulnerabilities and breaches, safeguarding their data and users.
Download the Checklist
Did you enjoy the blog but want an On-The-Go version? Check out our comprehensive security for a quick guide to safe software development practices.
Download The Checklist Here

Written by: Andrew Meyer
Andrew, a developer who started coding as a young kid, is passionate about learning, programming, and security. He has worked in game development and serverless Saas applications, gaining experience in various industries. Andrew’s great at cybersecurity, making sure software is more than safe. He describes himself as a Big Kid, curious about new technologies and loves to explore new ideas.

Edited by: David Galownia
David excels at propelling Slingshot towards their goals and oversees the strategic direction of the company. He’s been described as ‘intense, driven, caring, and passionate’ both at work and play. At work, he enjoys watching his team explore, imagine, and reinvent to do the best by their clients. At play, he drives Karts at insanely high speeds and scares his wife half to death. It’s all or nothing. Which means he gives it all.
Written by: Savannah Cherry
Savannah is our one-woman marketing department. She posts, writes, and creates all things Slingshot. While she may not be making software for you, she does have a minor in Computer Information Systems. We’d call her the opposite of a procrastinator: she can’t rest until all her work is done. She loves playing her switch and meal-prepping.
Edited by: Chris Howard
Chris has been in the technology space for over 20 years, including being Slingshot’s CIO since 2017. He specializes in lean UX design, technology leadership, and new tech with a focus on AI. He’s currently involved in several AI-focused projects within Slingshot.




